The basics: types of fraud
that start it all
FraudScore Approach
Fraud is a type of “crime” in any possible scenario. A marketer starts to dig his own pit when fraud is not detected. He invests more money on fraudulent channels that show great statistics, he gets unreliable sky-rocketing results and invests more funds on these channels. It’s a vicious circle of advertising and it needs to be broken.
Fighting fraud requires understanding and recognizing various types of fraud. This particular article is designed to give a quick overview of the types of fraud that are most common in the industry.
Click Spam
Definition and how it works
The fraudster tries to execute clicks for users who are completely unaware. The user might be organic to the app or an ad - but the fraudster uses different means to catch the last-action and get all the credit. The main method is to infect the device of a real user and get the click that provides real organic conversions.
How might the “infection” get to a real user’s device? Imagine, the user opens a mobile web page or an app and here is what might happen:
- Imitate the engagement - a fraudster can imitate user engagement by sending impressions-as-clicks. So it will look like the user viewed an ad and executed a click.
- An old trick - a simple real redirect of the user to the app-store page even if he hasn’t clicked on the ad of this particular application. This method uses promotional tracking links and is highly negative for the user as he directly observes that he is being redirected.
- Infected apps - various launchers, battery savers, screencasting apps, memory cleaners - these are the types of apps that are most likely to infect the user’s device and shall generate clicks whenever they want. They operate in the background and the user is never aware of that.
- Invisible threat or pixel stuffing - happens when a fraudster places various advertising links in the pixel in the background of mobile web page. These links shall be processed without showing any signs to the users. To illustrate - the most common case of pixel stuffing is mobile web pages where the user watches video content.
Standard symptoms
Low Conversion Rates or a long-tail for TTI graphs. Usually, a real user opens the app within the first 30 minutes to 1 hour post install. Of course, there are always exceptions to each and every case and source (and that’s why we suggest that you use FraudScore).
The problem that it causes
Click spam is a type of fraud when a fraudster is actually using real users to get credit. So if an advertiser invests in a source, observes a spiral effectiveness, impressive metrics - he shall invest more. But when it gets to the point where the budget is spent or being relocated from other sources (that in the end might appear to be fraud-free) but no profit comes of the source, then the advertiser begins to see the losses caused by click spamming.
2. Fake installs
Definition and how it works
Fake install - a completely fraudulent install by a fabricated user. This is one of the most
costly types of fraud because it spreads damage to all the possible parties – advertiser, network,
developer, and publisher.
The fraudster uses data centers and specific software to simulate
real devices. The main idea of such simulation is to create a brand-new “device” with its
brand-new ID, OS version, name just for the ad to be clicked on. Then, the scenario is simple –
“the device” just simulates a user-like behavior – click the ad, download the app, start the app
after the install.
Standard symptoms
Always check the price that you get for the traffic with other providers on the market. If the
price is lower than the average numbers on the market - chances are you are not getting what are
paying for.
And if you got into trouble, then you’ll need to take a look at:
- post-install-activity
- sometimes, at the pattern - if the majority or a significant group of your users follow the same scenarios and start the app in 5, 10, 17 days post install (e.g.) then they are likely to be fake
The problem that it causes
The main issue that this particular fraud type causes is when the advertiser pays for installs
and if he ends up paying for those that are fake - he simply pays for nothing. The same with the
network - if the installs that the network might get are fake and there are no actual users of the
installed app, then its reliability falls to the bottom.
And it’s worth mentioning that some
fraudsters have evolved in their activity up to the level when they attempt to emulate the
post-install activity of “the user” – e.g. start the app on the 10th or 17th day after install.
3. Click Injection
Definition and how it usually works
Only Android-devices are prone to click injection, a more complex type of click spamming. A
fraudster needs to have his own malware in the mobile app or even his own app to get access to a
real user’s device. After such infected app is installed it might get access to so-called
“installs broadcasts’’ – specific signals that are being sent by all new applications on the
device. And if the malware gets access to these signals, all the subsequent installs of apps from
the user’s phone shall be assigned to the fraudster.
Moreover, not all the apps have paid
marketing campaigns, so the malware has to check for those that do. So basically, click injection
requires a pretty complex approach but the treat is tempting so this type of fraud is consistently
detected by FraudScore.
Standard symptoms
Abnormalities in very low TTI, very high CR - these are the general symptoms of click injection. Since 2017, Google tries to provide developers and advertisers with more reliable data on apps and installs so that suspicious activity might be caught. But fraudsters are aware of that and the click injection schemes are becoming more sophisticated. So it’s hard to tell whether you are at risk of click injection just by looking at the symptoms sans fraud-detection tools.
The problem that it causes
The money of advertiser is spent on nothing. For instance, a developer buys traffic and the metrics show which GEO gives the most effective ads. Developer decides to invest more in the region. But in reality it turns out to be injected clicks traffic and basically the advertiser’s budget goes to the dogs. Injected clicks are also a problem for the network – because if the traffic is infected, the advertiser shall switch to another partner.
4. SDK Spoofing
Definition and how it usually works
The main principle is to imitate an install without a real one and to fake user engagement. But
fraudsters are using real devices – so no real users, no real clicks and installs, but perfectly
legitimate devices that exist and are being normally used by users.
A fraudster has his own app
(again, battery savers, memory cleaners, etc) installed on the user’s device or they might have
access to any other app that is popular and might be infected. By getting access to a real device,
fraudsters collect the device data, break the SSL encryption between tracking SDK and servers and
then they start a series of test installs.
So they make several attempts to find the install
combination and URL setup to imitate more and more installs. They simply need to find out which
activities in the app are being tracked and they start experimenting with the dynamic part of the
URL. If the fraudster detects the scheme, he can simply repeat it as many times as he can before
the SDK version will be updated and the fraudster’s scheme won’t work.
Standard symptoms
As we’ve already mentioned - the fraudsters break SSL encryption between tracking SDK and backend servers, so if the SDK is updated - the fraudulent activity shall stop. In our opinion, SDK spoofing is one of the most complicated types of fraud because it uses real devices’ data and fraudsters no longer need to constantly generate new parameters. We at FraudScore advice to check if SDK version of the installed apps match the latest release you’ve made.
The problem that it causes
There is no real install, no real activity in the app, in the ad or on mobile web-page, then there is no real user engagement. So the budget is being spent on nothing. A network might get pretty reliable metrics for app installs and might even show good results and user acquisition, but the results and further statistics shall show that this traffic is not to be trusted.
5. Device farms
Definition and how it usually works
One of the most famous fraud types and is pretty easy to understand – the devices are real, people who click and install are real too. But no profit comes from such installs – because the only purpose of the device farm is to get money for the initial install or click and never proceed with retention or purchases. People are hired to sit the whole day in front of dozens or even hundreds of devices and to repeat the same actions that they are all being told to do to get the clicks.
Standard symptoms
Sometimes, just looking at the retention rate, it’s obvious that there is a device farm that
generates this cluster of installs. But the problem is, that not all the apps have organic high
retention rates or time to start the app. So only a thorough analysis might help here.
We also
advice to take a look at IPs - some are well known to be unreliable, some try to mask and use VPN
or proxy - but a well-developed fraud detection platform shall trace such activity anyway and
detect those installs that are being made via suspicious IPs.
The problem that it causes
These are real devices, who are in fact real users, but are of no good to the advertiser or the
network. Such activity in only targeted to get the CPA budget of the campaign. And no future user
engagement shall ever be provided to the advertiser.
So again - be aware that if you invest in
mobile ads you would need to make sure that the traffic you get is examined by a fraud detection
platform, like ours for instance.
To conclude:
This particular article gives a short overview on several types of fraud that every company working with advertising is facing. The diversity of fraud types is vast. Just to illustrate, we’ve gathered and analyzed data for all the traffic that we’ve processed in August-November, 2018, and made a diagram for the distribution of types of fraud by seven main reasons:
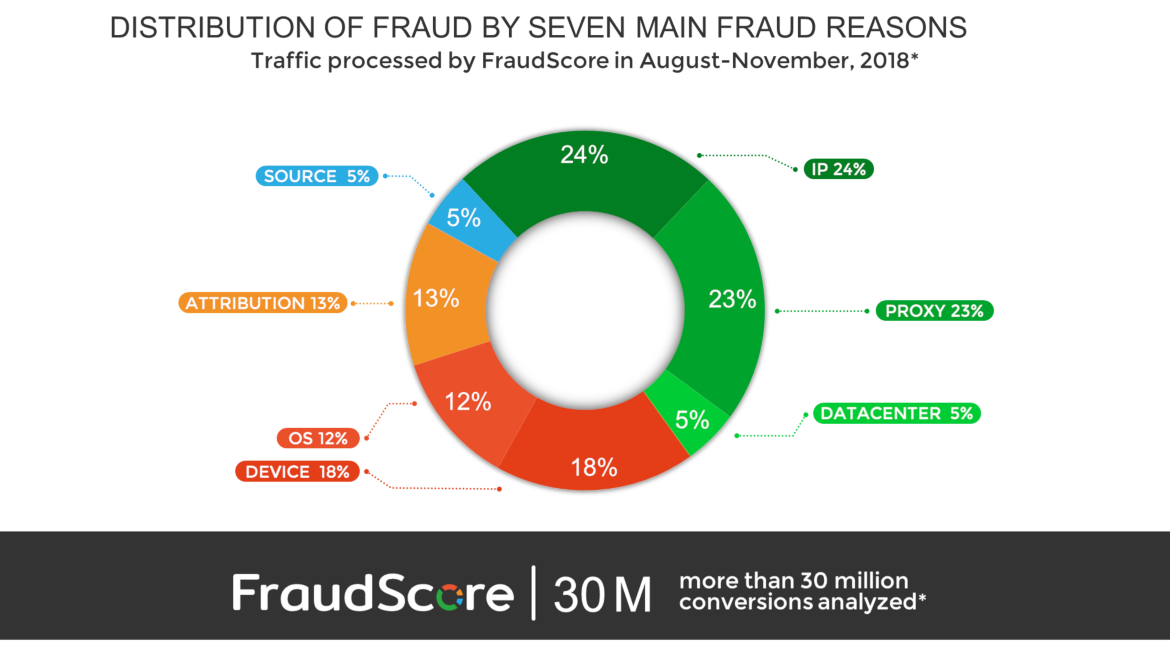
These fraud reasons demonstrate the diverse approach to fraudsters’ dodgery. Every category of reasons has its specific symptoms that we at FraudScore analyze and use as a source to detect fraudulent activities. We take a specific approach in order to analyze the symptoms and detect various combinations that contribute to systematic understanding and fighting fraud. If you want to learn more about how thorough and detailed our approach to traffic analysis might get, just follow the link to take a look.
We at FraudScore have set our goal - we fully take on the responsibility to detect and fight fraud that causes damage to our respectful customers. We are constantly interacting with clients and providing them with solid service and high fraud-detection expertise. We share our experience and it’s our firm belief that fighting fraud does not only require raw statistics and metrics, but it also requires knowledge and constant education.
Ad fraud is a problem and the industry has finally shifted towards recognition of its gravity. Everybody is affected: a network loses trust in publishers because of fake installs, a marketer keeps spending funds on those channels that are not truly effective, etc. It might really become a vicious cycle unless fraud is detected and banned.